When you browse the web in your laptop or mobile device, you find your comfort zone and make sure anybody in the office, room or establishment, in general, can see what you are doing in your online sessions. Or so you think.
Usually, workers prefer to choose PCs in corners, or in places where nobody can spy on their content. It doesn’t necessarily mean that the person in question is doing some shady things online; it is more like protecting himself/herself from prying eyes.
However, the truth is that your Internet Service Provider, or ISP in its short version, can have access to certain data and traffic you exchange with networks and websites. The real question, then, is: What can your ISP see and what kind of content or information is kept from it?
ISPs Keep Mandatory Data Logs of EVERYTHING

In countries with heavy Internet censorship, the government may oblige ISP to keep data logs to make sure some sites aren’t opened or visited and to have the proper support and proof that a person went to a specific page.
On the other hand, many ISPs serve as allies to big Internet companies, retailers, shopping sites, and other businesses: they provide data about some users’ browsing patterns, history, and favorite sites, with advertising purposes. If you spend your days looking at online platforms to buy soccer equipment, or petrified wood tables, don’t be surprised to find such ads in the future.
Of course, not everybody tolerates that kind of invasion of privacy. That is why people often look for the most remote computer in an office in the first place: people don’t like its peers looking at what they are doing, so each day, more and more tools rise up the scene to combat the ISP snooping issue.
Hide Traffic, Content, and Data from ISP with a VPN
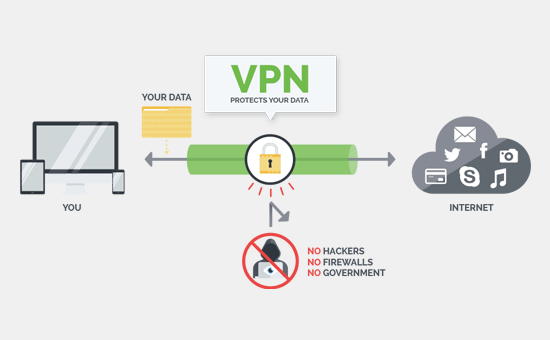
The most widely spread tool to avoid ISP snooping with effectiveness is the use of Virtual Private Networks or VPN. They are online resources consisting of encryption methods and measures that can help the user hide important information about their connection, such as their IP address, browsing history, and more.
To encrypt the content, the VPN provider uses protocols. Some of the most popular and effective is the OpenVPN technology, Internet Protocol Security (IPSec,) Layer to Tunneling Protocol (L2TP,) and the Secure Sockets Layer (SSL.) The VPN technology is based on the once reliable, but now superseded Peer to Peer Tunneling Protocol, or ‘PPTP.’
The encrypted content is rerouted to remote servers, away from the prying eyes of the governmental institutions making surveillance on your content, hackers trying to steal crucial data and passwords to penetrate your security systems, viruses and malware lurking around the web and; most importantly, your Internet Service Provider.
- How does a VPN hide information?
VPNs are online services that an average person can hire to gain privacy, security, anonymity, and accessibility. By hiding the user’s IP address, it makes him/her practically anonymous on the web, increasing privacy and security at the same time. The accessibility gains are associated with the VPN ability to unblock restricted international content from anywhere in the world.
- What do VPNs unblock?
VPNs allow you to access content that would otherwise be blocked by masking your IP address and letting you choose another one from a country of your liking, as long as it is within the list of available nations/servers. For example, if you want to enjoy the BBC iPlayer, but you are in Mexico, you can connect to a server from the UK thanks to your VPN client and the service will become available to you because the geographical restrictions associated with a British IP address would be lifted.
Most of the reliable VPN options don’t cost a fortune: in fact, some of the top alternatives are priced at less than $14 per month, which is a fairly affordable number considering that it can be the value of an average meal in most countries.
The magic of VPN can keep your ISP away from your content, because you will be on the web with an IP address different than yours, and most of the content will be off-limits to them and their various intentions.
What exactly can your ISP see?
Lots of things, actually. Your Internet service provider has the ability to identify which IP addresses you contact, which basically means that they can see which pages you are visiting at any given time.
- How does a VPN “hide” information from ISP?
ISPs can also know everything you send that isn’t protected by encryption. Internet companies and providers collect metadata, which is any set of data that describes and provides information about other data. They are mostly ports and IP addresses, but they can identify how much time you have been connected and the amount of data you have sent in your session.
- What does an ISP collect and how do they use it?
The thing is that metadata, with a little effort, can lead to important information about you and your connection. Your ISP, if they choose to, can learn who you are exchanging communications interactions with and whether you sent an email or visited a specific page.
Regarding content they can or can’t access, yes: they can manage to learn what you write in your emails and the pages you enter, but another fair and pertinent question would be whether they care enough to decipher the metadata and look for further data.
- What do ISPs “do” with data?
Basically, there are two things that matter to ISPs: money, and not getting in any kind of legal issues. The former is why they sell your traffic and most visited pages to the highest bidder, and the latter is why many of them, especially in nations with heavy Internet censorship, keep logs of your data.
For example, Internet service providers living and performing business operations in the United States of America can only share content with their clients or users with the government, not with advertisers or other companies. However, they can share your metadata with virtually anybody, and that is why you need to protect yourself.
- How to Stop ISPs from Collecting Data Without VPN?
Another issue is that privacy policies on these providers are usually written ambiguously, so any attempt to gain further clarity in which data can they keep and share is a futile one. In addition to that, ISPs can store metadata for any period of time ranging from a few months and a couple of years.
What can you do to protect yourself from your ISP?

You can implement Tor, which is a browser that encrypts your traffic. However, it can be extremely slow so users need to be prepared to activate other options. Smart DNS proxy servers can also help. However, the best measure you can take to protect yourself from the snooping from your ISP is hiring the services of a quality VPN. The Internet universe is filled with good, bad, and mediocre options, but the good thing is that some of them are free. You get what you pay for, though.
Best Option to Stay Secure with ISPs?
The most reliable client you can hire is TorGuard. It has the safest encryption and all of the most commonly implemented protocols while providing users the ability to connect up to five different devices at the same time.
TorGuard has many services aimed to improve the privacy of its users, such as an anonymous email, anonymous VPN, anonymous proxy and a privacy bundle. As the cherry on top of the cake, TorGuard has more than 3,000 servers located in 55 countries around the world.
In conclusion, your ISP can be able to see and collect metadata about you and your connection, and you may not like it. You could find yourself forced to take privacy measures, and the most opportunistic one you can adopt is the use of a VPN.
VPNs can encrypt your traffic in such a way that your ISP will only be able to see indecipherable information getting sent and received between your PC or device and a VPN server. Your ISP may see that you are establishing a connection with a distinct address, but your traffic will be mostly protected.
