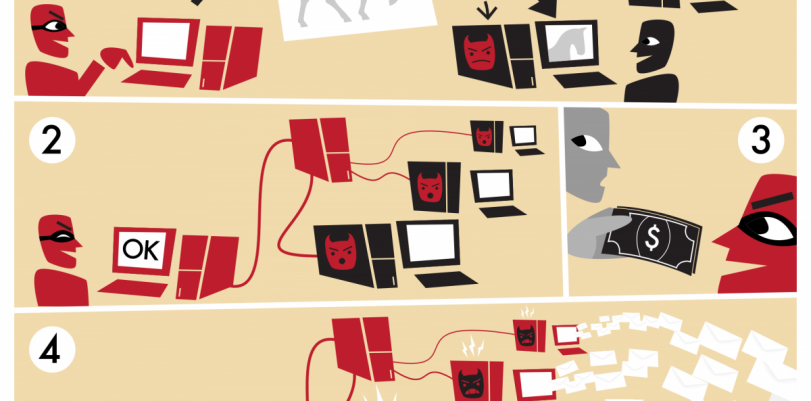
A botnet, which is a combination of “robot” and “NETwork,” refers to inter-connected devices with each component running single or multiple bots. Their use is thoroughly associated with malicious and dangerous activities, such as Distributed Denial of Service (DDoS) attacks, data theft, spamming, and the allowance of access to devices and connections by the person behind them.
Usually, the botnet owner has the ability to control it with C&C (Command and Control) software. The inter-connected devices can be smartphones, computers, or even IoT (Internet of Things) powered gadgets or appliances.
In a botnet, the devices in question have been breached, and their control has been passed to a third-party. The “infected” or “controlled” gadgets are the “bots” and have fallen in that condition because of the action of malware-infected software distribution.
The aforementioned scenario lets the botnet owner or controller mandate commands and direct which activities they are going to perform. It uses communication methods or channels formed by standards-based network protocols. IRC and the Hypertext Transfer Protocol (HTTP) are some notable examples.
In our current data and online security landscape, the proliferation of botnets is seen as threatening and dangerous, since cybercriminals and hackers are renting them with increasing frequency to perform their shady purposes.
Botnet architecture
Like the viruses that go into the human system and tend to earn immunity when they aren’t treated correctly, botnets have also evolved and developed skills to avoid being detected and disrupted.
Bot programs are created as clients, with server-enhanced communication methods. That scenario lets the bot herder, which is the person or entity that controls the botnet, to exercise control over specific devices from remote places, effectively obfuscating traffic.
However, more recent botnets are depending on already existing peer to peer networks to establish communications. They are called P2P bot programs, and they have the advantage of not needing a central server to communicate, whereas the client-server model does have that requirement.
Why are botnets bad?
Botnets have reached headlines in the most influential media outlets in recent times for a variety of reasons. Nowadays, most discussions about cybersecurity land on the subject because of a few prominent scandals involving the use of botnets.
For example, Facebook was involved in a fake ad controversy. Twitter, as well, had a role in the botnet scandal that surrounded the 2016 presidential elections in the United States. The disruptive potential of botnets has been evident in those cases, raising concerns in several industries and communities.
Social media bots and fake, or automated accounts, can be very effective spreading false news to try to swing the masses into on “side” of the story, without even worrying about the legitimacy of the information being published.
On top of all that, botnets can also be used to mine for cryptocurrency. Bitcoin mining is an increasingly profitable business interest for cybercriminals, and they often infect computers within a network with software destined to mine without authorization and exhausting all the device’s resources and processing power. They can also steal digital wallets.
The malicious use of botnets is also threatening and hazardous for corporations and international companies of all sizes because they can also infect devices with malware, initiate DDoS attacks, incur in scams, fraud, and identity or data theft.
A few notable things about botnets that you should know
- Bot herders need their botnet to be as broad as possible, because the bigger it is, the bigger the impact. That is why they want several devices, or bots, connected.
- Botnets are usually designed to infect millions of computers and devices, not just one.
- Herders deploy botnets through Trojan horses, making the user infect itself by clicking on a dangerous attachment or popup.
- However, more advanced botnets can also self-propagate, spotting and infecting devices automatically.
- They are tough to detect.
- They can infect almost any device connected to the internet, no matter if it is directly or via Wi-Fi. That includes personal computers, laptops, mobile devices, smart watches, security cameras, and smart kitchen appliances like fridges.
How to prevent botnets
- Keep your operating system up to date.
- Don’t click on email attachments from unknown sources.
- Don’t download from P2P and file sharing networks, and avoid torrenting if you can.
- Avoid clicking on suspicious links.
- Don’t forget to get antivirus software.
VPNs: an additional layer of security and data privacy
 |
 |
|
|---|---|---|
| Multi-platform Compatible | ||
| 256-AES Encryption | ||
| PRICE | $5 for 1 month with code "best10VPN" | $6.95 a month |
| Website Rating | 9.9 | 8.8 |
| 24/7 Live Chat | ||
| Residential / Dedicated IP for permanent streaming access | ||
| Has Mobile App + PC / Mac Support | ||
| Stealth VPN / Advanced Obfuscation techniques | ||
| Visit VPN Provider | Visit TorGuard | Visit PIA |
As an extra safety and privacy measure, you can opt to implement a Virtual Private Network or VPN service. It comes in the form of apps or clients provided by online security companies around the web, and it can help you gain anonymity so that threats such as botnets, hackers, and malware developers can’t reach you as quickly as if you were unprotected.
VPNs can implement protocols to reroute and hide your most sensible traffic, including your IP address and shared content online. They also come, according to the provider, with impressive security measures such as DNS leak protection, split tunneling, a kill switch, and much more.
A VPN’s primary intention is to provide security and private browsing. They can also help users dodge censorship measures, governmental surveillance, and online advertisers, which is a safety gain.
There are hundreds of VPN brands in the market that can offer varying types of service with different levels of efficiency. However, the most reliable of them all is TorGuard, because of its military-grade 256-bit encryption, multiprotocol availability, and the ability to connect five different devices at the same time.
On top of that, TorGuard has more than 3,000 servers in 55 nations around the world, a perfect setting for unblocking content that falls under geo-blocking restrictions. A strict no logging policy protects the user’s privacy.
In conclusion, botnets are dangerous elements that can inflict damage in several ways. Understanding what botnets are and knowing how to deal with them will go a long way in protecting the user’s digital assets, privacy, and security.