Most people are acquainted with the regular Internet service, the one those in the dark web know as Clearnet because it is unencrypted. However, the online world goes well beyond that, as it has hidden sites and services that you wouldn’t imagine.
Under the surface of what your search engine shows as natural results is an enormous amount of content, sites, and services known as the dark web. You should know that to access it you need to use encryption software like Tor or I2P.
You may ask yourself why is it all hidden? Are those sites illegal? Well, not necessarily. Sometimes, the government or other authorities consider these sites aren’t apt for mainstream review, and they prefer to keep it beneath the surface.
The dark web per se is not dangerous, but some of the activities you may perform while you are in there may be. In this guide, you will know a bit more about what you should and shouldn’t do while you browse the web within the network.
WARNING:
Whenever you’re using the dark web, you should make sure to use a VPN so you IP and internet activity stays anonymous and hidden from other users–whether malicious or not.
Check out these top VPNs below:
 |
 |
|
|---|---|---|
| Multi-platform Compatible | ||
| 256-AES Encryption | ||
| PRICE | $5 for 1 month with code "best10VPN" | $6.95 a month |
| Website Rating | 9.9 | 8.8 |
| 24/7 Live Chat | ||
| Residential / Dedicated IP for permanent streaming access | ||
| Has Mobile App + PC / Mac Support | ||
| Stealth VPN / Advanced Obfuscation techniques | ||
| Visit VPN Provider | Visit TorGuard | Visit PIA |
What is the Dark Web?
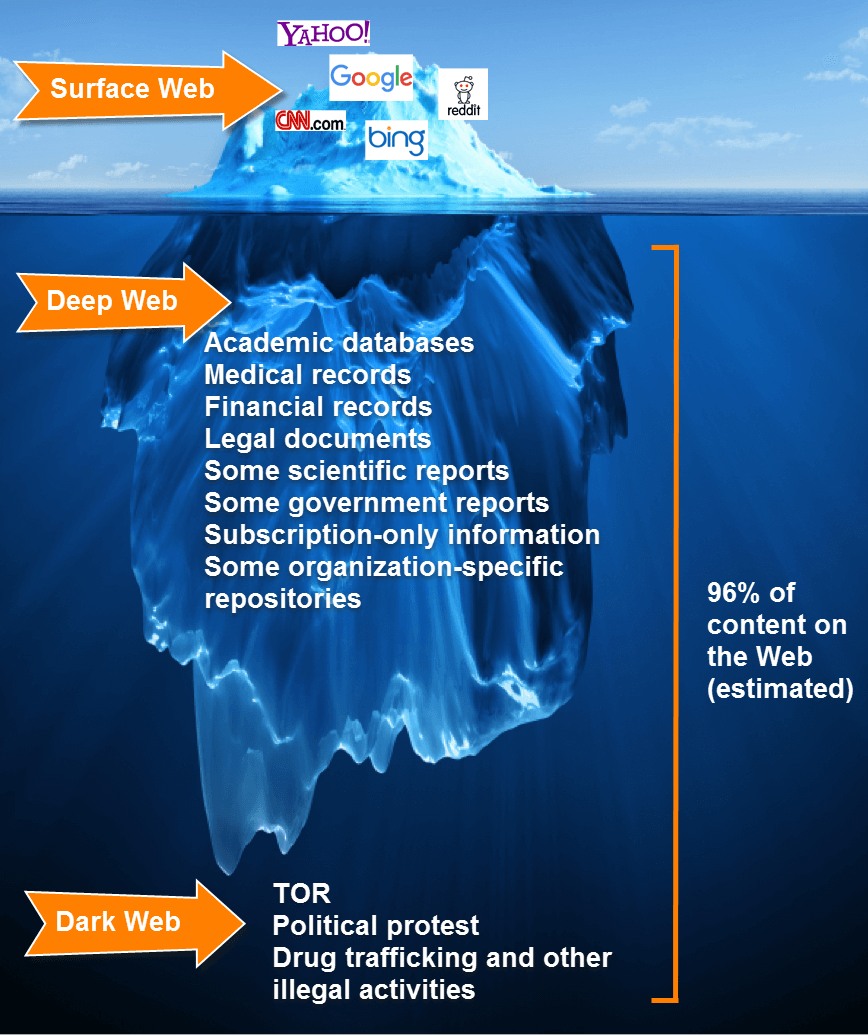
The dark web is a part of the World Wide Web, one that functions because of darknets and overlay networks. They require Internet, but the method to establish connection implies specific authorization measures to access other configurations, and precise, specialized software. Not everybody is allowed in some of these pages.
More often than you would imagine, the dark web gets mixed up with the deep web. The latter is a much broader concept that refers to the part of the Internet not shown by search engines. The dark network is a subsection of the deep web.
The dark web, in turn, interacts with the darknets, which are the environment that contains the former. The latter include peer to peer networks or much broader services, such as Tor, I2P or Freenet. As part of the usual language used in the dark web, people call the regular, unencrypted Internet connection “Clearnet,” and the Tor software receives the nickname of Onionland.
Overall, you can only access darknet websites through the Tor network and I2P (Invisible Internet Project.) Tor and its related services are known and identified as .onion domains. They have slightly different approaches: Tor is obsessed with anonymous browsing, while I2P guarantees anonymous website hosting, such as blogs.
Dark web services: Tor, Freenet, and I2P
Tor
Tor is a network that promotes anonymous communications and web browsing. It is free, and its name origin is related with the initials of the phrase “The Onion Router.” Tor works in such a way that it can guarantee total anonymity in online sessions.
Tor “relays” traffic thanks to a free and volunteer overlay network. In total, almost eight thousand relays are working together to divide data into small chunks, a process that makes it almost impossible for prying eyes to understand.
The relaying network has worldwide-reach, and it conceals a user’s location from virtually any external agent trying to do surveillance. As a result, nearly all activity and traffic generated on Tor is protected from spying, including sending emails, browsing the web, and social media.
Tor protects the privacy and anonymity of its users, but the most prominent downside of its use is the slow speeds that result from the continuous overlaying of data. Streaming in Tor is nearly impossible, and it doesn’t allow P2P activity (torrenting) either.
Freenet
Freenet’s primary objective is to provide a platform that can resist even the most robust censorship measures that some governments, in their quest to suppress freedom of speech or defend “national interests,” may apply to its citizens.
Technically, Freenet is a peer to peer platform that uses decentralized distributed data store in a similar way than the blockchain technology to keep information and deliver it. Some of its most common applications are microblogging, media sharing, blogging, and a web of trust for decentralized spam resistance.
I2P
In a similar way than Freenet, the I2P (Invisible Internet Project) promotes a censorship-free environment in which users from all over the world can interact and browse the web without having to worry about getting caught. It allows an instant peer to peer communication by traffic encryption. I2P sends this shared data through a 55,000 computer network.
Web-based hidden services
- Gambling
- Guns
- Chat
- Not yet indexed categories
- Abuse
- Books
- Directory
- Blog
- Porn
- Hosting
- Hacking
- Search
- Anonymity
- Forum
- Counterfeit
- Whistleblower
- Wiki
- Bitcoin
- Fraud
- Market
- Drugs
What you should do while browsing the dark web

Use Tor to start your dark web experience
The Tor network is the best way to start your ventures in the dark world. It is easily downloadable and is free while being compatible with the Windows, Mac and Linux operating systems. The setup process is also very straightforward and perfect for newcomers.
Use directories to enhance safety
Since you need to start finding your links to browse the dark web while being inside Tor, you should use directories to surf safely and with a keen sense of responsibility. Remember, you are not at your house’s backyard! You are in a potentially dangerous environment. Use the Hidden Wiki (a directory full of resources,) which you can access by clicking on http://zqktlwi4fecvo6ri.onion.
Take your time and assess what may be illegal and what can be deemed safe to surf. The Hidden Wiki can help you access useful links to Onion websites.
Have fun and join a book club
There is also space for literature on the dark web! Book clubs have been a thing there for quite some time, and people can search for options such as the Jotunbane’s Reading Club and the Imperial Library of Trantor. Of course, some people actively download illegal copies of books and pieces, but there are some passionate, heated discussions to be found.
Discuss controversial issues, such as the end of the world
Some religiously strict countries and societies find the end of the world to be a controversial issue. In the dark web, you can see places to prepare for it: for example, the Strategic Intelligence Network provides information on the matter of possible crisis management, from wars to natural disasters. The Hidden Answers work, too, as they are the “dark web equivalent” to the Yahoo! Answers. You can ask questions about drugs, erotica, war, politics, governmental and intelligence issues.
Get Social
There are social media outlets on the dark web, and they can be similar than those in the “Clearnet,” only with a higher anarchists ratio. Operation Genesis is a perfect example. There are also games to play online and email services such as Anonibox.
What you shouldn’t do while browsing the dark web

Open “.onion” sites on anything other than Tor
By connecting to services such as Onion2web or Tor2Web from your Google Chrome browser, you may access .onion pages, but your IP address can get exposed, and your online security will suffer. Use the Tor browser if you want to enter the dark web.
Enabling macros and scripts
Try to stay away from enabling JavaScript or other macros and scripts. They can derive in unwanted risks to your online security. You should only make exceptions to world-famous sites such as Youtube.
If the site is not trustworthy, enabling scripts and macros can result in your system automatically downloading a Trojan or any other form of malware. Your performance will suffer, you will see a lot of pop-ups and annoying ads.
Downloading files from shady or unknown sites
As obvious as this may seem, we are in the obligation to remind you that unknown attachments and downloads can compromise your computer. Be always alert for automatic downloads. If you have to download a file, use a virtual machine like Virtual Box.
Mistake deep web with dark web
The Deep Web is not indexable by regular search engines, whereas the Dark Web is not separate from the Deep Web, but rather a portion or subsection of it. Specifically, it’s the one that neither standard search engines nor web browsers can enter.
Thinking it’s inherently legal
If you believe that the dark web itself is not illegal, you may be right. But numerous acts and performed in there are shady. Why do you think it is called as such? Drugs web pages, weapons information and commerce, hacker activity and hitmen all interact on the “other side.” You are fine in the deep web, though.
Buying goods or services from a darknet market
You can buy things on the dark side: the problems, though, may arrive if you get caught. And you should be wary because some of the e-commerce page managers can be covered law enforcement agents ready to take you down. Also, the environment is suitable for thieves, scammers, and fraudsters.
Using your credit or debit card
If you purchase things with your credit or debit card, the possibilities for criminals and hackers to gain access to your numbers or information are somewhat high. Try to use cryptocurrency, such as Bitcoin, if you must buy something o the dark web, as it is tough to track transaction details.
Making friends or enemies
As you know, making friends in the dark web is not a very good idea, since when you least expect it, you may find out that they “betrayed” you because they can be agents. Also, it would be beneficial if you didn’t make any enemies as well, as you don’t want some retaliation attack. A low profile is the best approach.
VPN and Tor together
While VPNs focus on privacy/security and the Tor browser’s motto is anonymity, these two online resources and tools can correctly work together to cover up each others’ shortcomings and protect you on your sessions.
You can hide your identity with both, but using Tor would mean that anyone will have access to your activity while you may have to trust your VPN in that matter, as it has to be able to see your logs to protect you. However, VPNs are way faster than Tor, and they also provide geo-blocking avoidance. Virtual Private Networks also allow P2P activity and torrenting, something that Tor can’t brag about.
In conclusion, the dark web may be a fascinating environment that combats censorships and gives space to anarchists, but beware: there may be illegal stuff going on there, so knowing what you can and can’t to is a crucial aspect of the experience.
