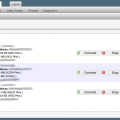
How to Use OpenWRT router for torrents with LuCI interface
OpenWRT is a firmware based on Linux. It works best on a router, and it distributes embedded devices. It doesn’t function as a static firmware: users can manipulate OpenWRT and configure different kinds of things and services. Users can write and modify the writable system of files that OpenWRT features managing data packages. It means that this firmware is fully customizable, and you can do...[Read More]
How to Watch EPIX Outside the USA
The wave of video on demand options on the Internet is deeply related to the world’s need for entertainment and leisure options. After all, our everyday life is so agitated and fast-paced that we need time to relax with a good movie, a sitcom, or a fascinating documentary. Understanding the people’s need and providing entertainment solutions to get people out of boredom motivated the l...[Read More]
What is the Best VPN in Vietnam to Unblock Censorship?
Vietnam has a unique place in the world’s history books. The country endured some tumultuous years in the fifties, sixties, and seventies with the Vietnam War, but nowadays, it has experienced sustained economic growth. Although there are enormous disparities in the wealth distribution, it is safe to say that Vietnam is in a better position than some of its Asian neighbors. However, Internet...[Read More]
The KRACK Vulnerability: What it is and How you can Protect Yourself
The KRACK is a severe vulnerability found at the WPA2 encryption level of Wi-Fi connections, which is the most widely used around the world. Mathy Vanhoef discovered the KRACK vulnerability last year, and since that moment, terror has been spreading in the Internet world. The WPA2 protocol is the one in charge of encrypting your data and traffic in a Wi-Fi hotspot. With the recent vulnerability, h...[Read More]
What are the Best Zenmate VPN Alternatives?
VPN is one of the most prominent inventions of the late nineties technology-wise. Virtual Private Networks are online resources which primary function is to enhance the user’s privacy, anonymity, and security when browsing the web. This technology was introduced in 1996 when a Microsoft worker famously developed the Peer-to-Peer Tunneling Protocol (PPTP), the father of VPN. It functions by t...[Read More]
What are the Best VPN Routers to Use?
A VPN enabled router is a device that can share Internet and support VPN encryption and security protocols at the same time. These tools allow users to achieve better connection speeds and browsing the web securely and privately. A startup or small business venture may only need a regular router. However, if the enterprise network hosts more than three devices connected at the same time, it may be...[Read More]
How to Use Any VPN On Amazon Firestick – Easy Guide!
Entertainment is one of the most sought-after features on the Internet. People of all ages often look to stream online content, read an eBook, enjoy a multiplayer game, read the daily news and engage with thousands of friends in social media. Online streaming, which is now one of the preferred entertainment methods, doesn’t necessarily have to be done through a personal computer, a Smartphon...[Read More]
When was VPN Invented? Learn About the Origins of the Tunneling Protocol
Privacy and security have long been some of the essential needs of the human race, in all ventures. With the rise and popularity of the personal computers, the Internet, smartphones, tablets and other gadgets, the search for those two characteristics is even more intense. Virtual Private Networks appeared on the scene as tools that could help users achieve a more secure connection, hiding its traf...[Read More]
How to Protect Yourself from Ransomware with a VPN
Browsing the web may seem like a fun thing to do. And it is! You can do hundreds of tasks on the Internet: play games online against a computer or other players around the world; stream music, videos, TV series, shows, documentaries, and even live sports events with ease. You can read the world’s latest news, check the results of that game you missed, enter and enjoy dozens of social media o...[Read More]
Can a VPN Protect You Against Computer Viruses?
Computer viruses have been wandering around the web universe for a very long time. Some people are extremely cautious with their online activities and interactions, while some others fearlessly click on every ad they see and download any attached content in their email inboxes, without even knowing who the sender is. Letting a virus enter your online assets and software could have catastrophic con...[Read More]
VPN vs. Firewall – Which is Better and for What?
In the discussion about which security measure is better for your desktop computer or mobile device, firewalls and Virtual Private Networks often get the first two spots, meaning that they are the two preferred ways to protect one’s assets online. Antivirus software can also be useful, depending on what you are trying to achieve. Each method has its advantages and disadvantages, but a combin...[Read More]